The excessive technical language used in cybersecurity creates a complex system which forces people to use outdated security methods that depend on their personal judgment. The false security created by these myths enables hackers to break into your personal data systems with greater success.
“I’m not a target because I have nothing to hide”

Hackers target your computer system because they want to access your processing power and email address which they can use to send spam and your identity which they can use to open credit accounts. Every person possesses “digital value” which automated bots search for online to find individuals who maintain weak security systems.
“Incognito Mode keeps me anonymous”

The “private” and “incognito” functions only stop your browser from keeping track of your browsing history on the device you are using. Your ISP and your employer and the websites you visit can still monitor your online behavior while they obtain your IP address.
“My Mac can’t get viruses”

Growing Apple product use has shifted cybercriminal activity from Windows systems to target Mac machines. Macs become infected with both malware and ransomware threats. Brand name products should not be treated as complete security solutions because users face serious security risks.
“Strong passwords are enough”

A lengthy password becomes vulnerable to theft during data breaches and phishing attacks. The Multi-Factor Authentication (MFA) system which requires your phone approval for password login serves as more crucial security than the password itself. The physical lock system prevents digital hackers from easily accessing your digital resources.
“Antivirus software makes me 100% safe”

Antivirus software operates like a seatbelt which protects you during crashes but it does not guarantee your total protection. The modern “zero-day” attacks have developed methods which enable them to bypass all existing software protection systems. You need to maintain safe browsing practices while your software should remain current.
“Hackers only target big businesses”

Hackers find small businesses and individual users to be their most attractive targets because both groups maintain insufficient security measures. Small-scale cyber attacks depend on automated systems which do not distinguish between Fortune 500 companies and local bakeries.
“I’ll know immediately if my phone is hacked”

The newest malware programs function as “silent” threats. The program needs to operate in stealth mode which allows it to collect sensitive information without consuming system resources.
“Public Wi-Fi with a password is safe”

A password protected coffee shop Wi-Fi system does not stop other network users from accessing your data packets through “sniffing” tools. Public Wi-Fi usage requires you to implement a Virtual Private Network (VPN) which will secure your entire internet connection.
“Buying a ‘Secure’ device is a one-time fix”
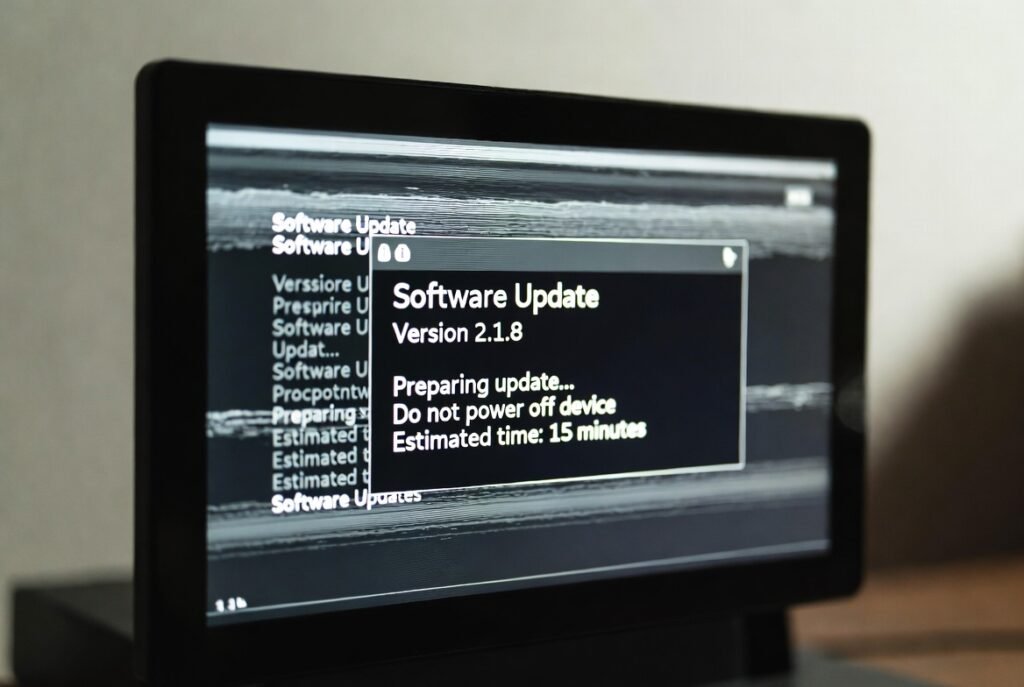
Security requires ongoing maintenance because it exists as an ongoing procedure instead of a single security product. The “secure” phone you possess today needs security patches to function properly tomorrow. Outdated software exists as the primary method for hackers to gain access to “secure” systems.
“I don’t need to worry about ‘About Me’ quizzes”

The social media quizzes which ask for your first pet’s name and your mother’s maiden name function as “social engineering” traps. Password recovery systems at banks use these security questions which show your publicly disclosed personal data to hackers who want to reset your password.


