Online gaming often links progress, purchases, and social status to digital accounts. A long time player began noticing subtle disruptions during routine play. Small inconveniences appeared across launchers, multiplayer lobbies, and in game stores. Each issue looked minor in isolation. Combined patterns pointed toward weak protection. This article outlines specific warning signs observed during gaming activity, showing how routine habits exposed serious gaps across account security.
Unfamiliar Login Alerts After Normal Playtime
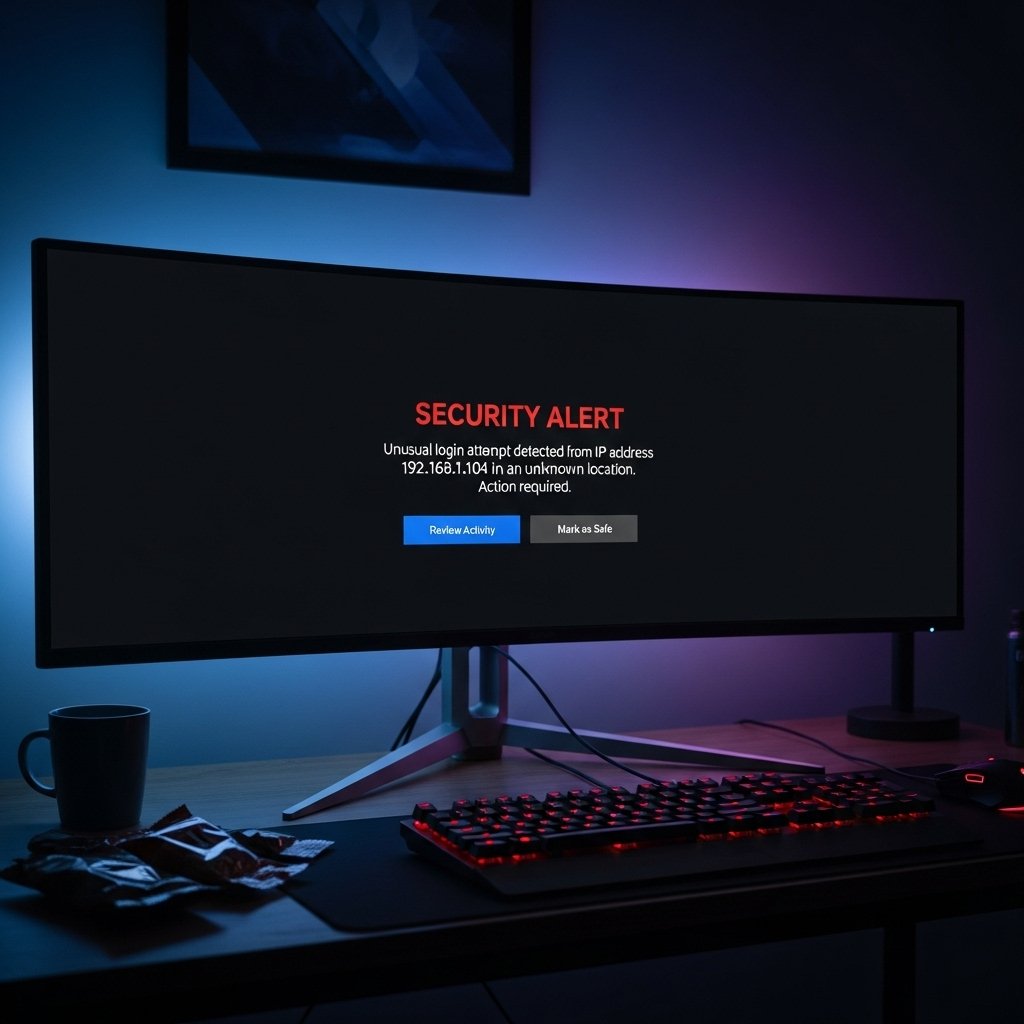
Late night sessions triggered alerts from a major launcher linked to Steam. Messages referenced access from locations never used by the player. No travel occurred during those dates. Repeated alerts suggested external access attempts rather than system errors tied to network changes or updates.
Friends Reporting Random In Game Messages

Teammates inside Fortnite reported strange chat messages sent during offline hours. Language differed from usual tone. Timing conflicted with work schedules. Message logs revealed activity during early morning hours, indicating third party access through compromised credentials.
Unexpected Changes to Game Settings
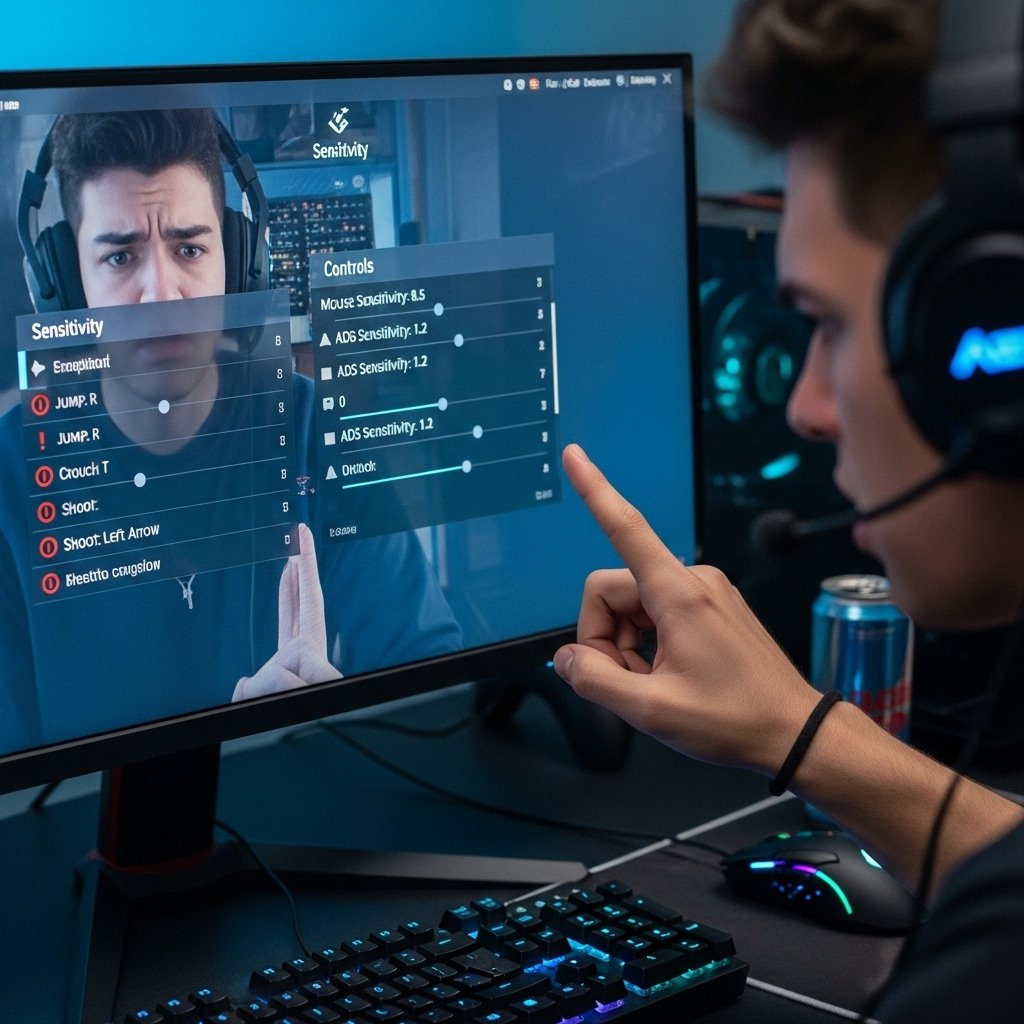
Control layouts, sensitivity values, and graphic presets shifted without user action. Competitive matches suffered due to altered configurations. Reset attempts failed after relaunch. Recurrent changes implied unauthorized access through synchronized cloud profiles linked to the primary gaming account.
Missing In Game Currency and Items

Premium currency balances dropped without recent purchases. Inventory logs showed trades never approved by the player. Support tickets revealed activity from unknown sessions. Virtual items tied to real spending raised concern about financial exposure beyond simple gameplay inconvenience.
Password Reset Emails Without Requests

Multiple reset notifications arrived across email and launcher accounts. No reset actions originated from the user. Frequency increased after major update releases. Pattern analysis pointed toward automated credential testing common across gaming platforms with reused passwords.
Slower Matchmaking and Account Restrictions
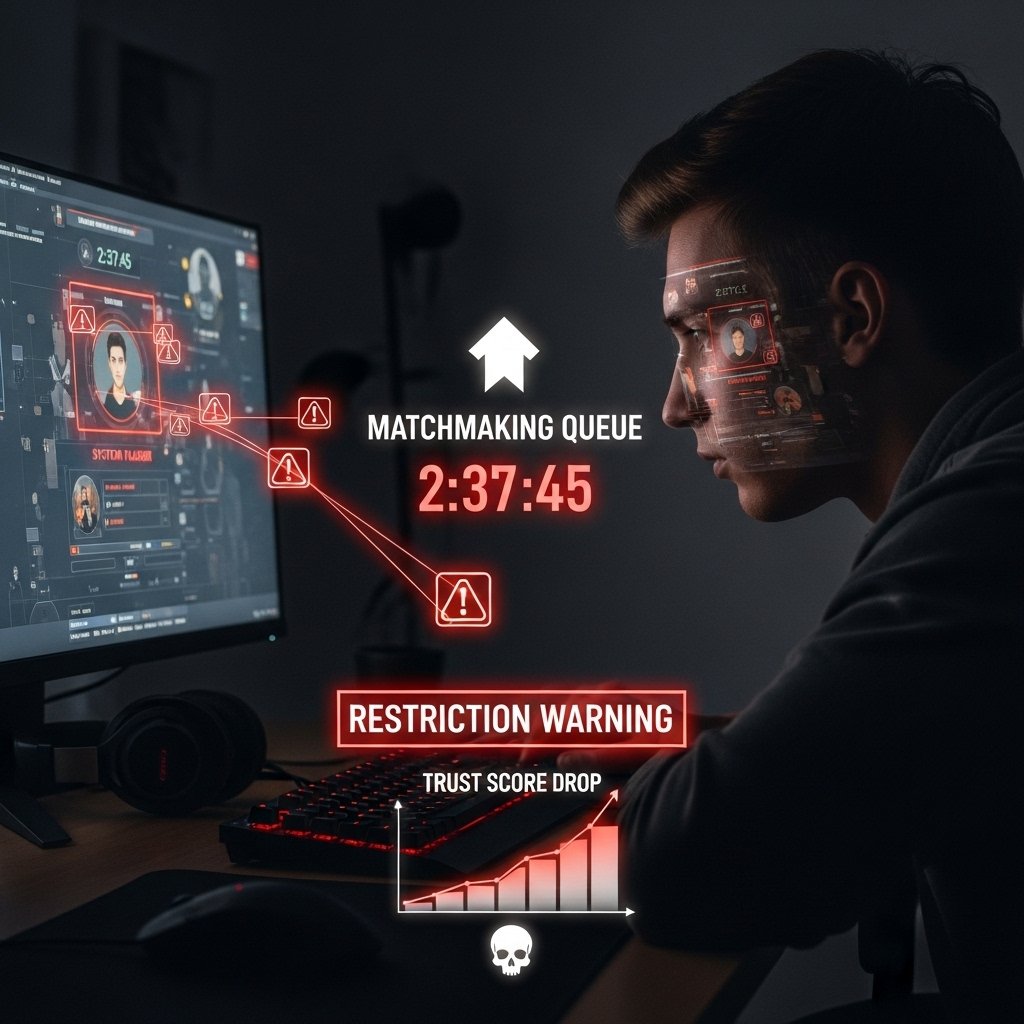
Queue times increased without rank changes. Temporary matchmaking limits appeared after reports from other players. Investigation showed suspicious behavior flags triggered by unknown play sessions. System trust dropped due to irregular login patterns rather than performance metrics.
Third Party Sites Requesting Reauthentication
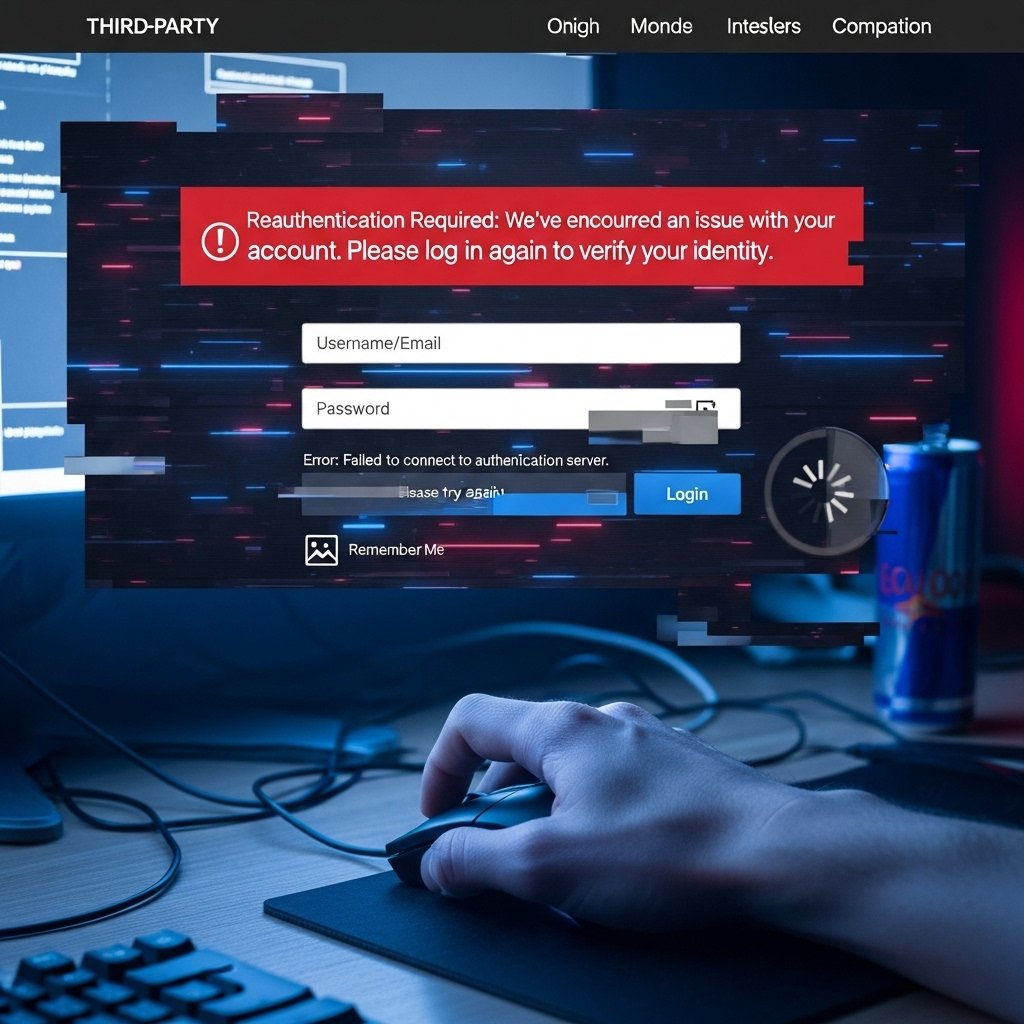
Esports stat trackers and mod platforms requested repeated logins. Tokens expired faster than expected. Some sites denied access despite valid credentials. Linked account security breakdowns disrupted trusted integrations across the gaming ecosystem.
Email Account Showing Gaming Related Activity
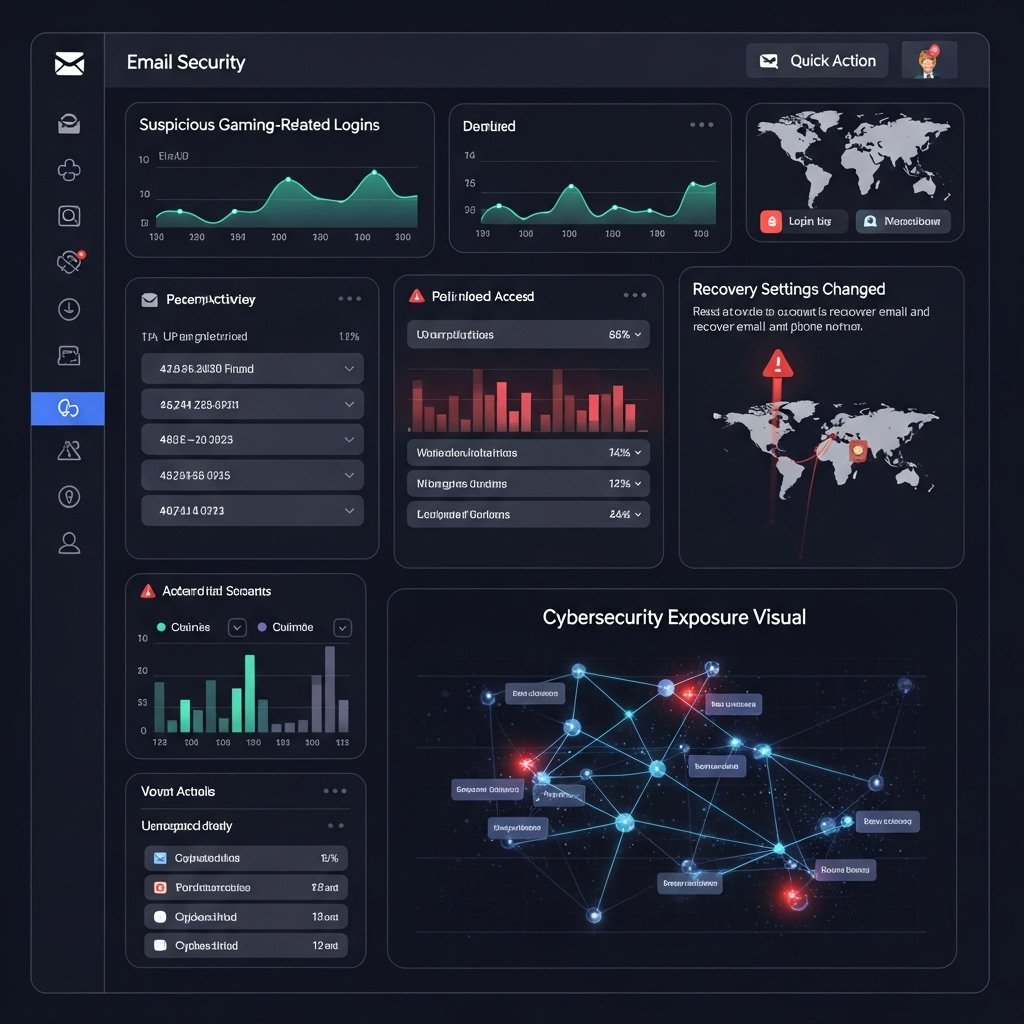
Primary email inbox logged sign ins connected to gaming alerts. Recovery settings changed without approval. Security logs displayed access times matching earlier launcher warnings. Email compromise expanded risk across every linked gaming service.
Mobile Authenticator Prompts During Offline Hours
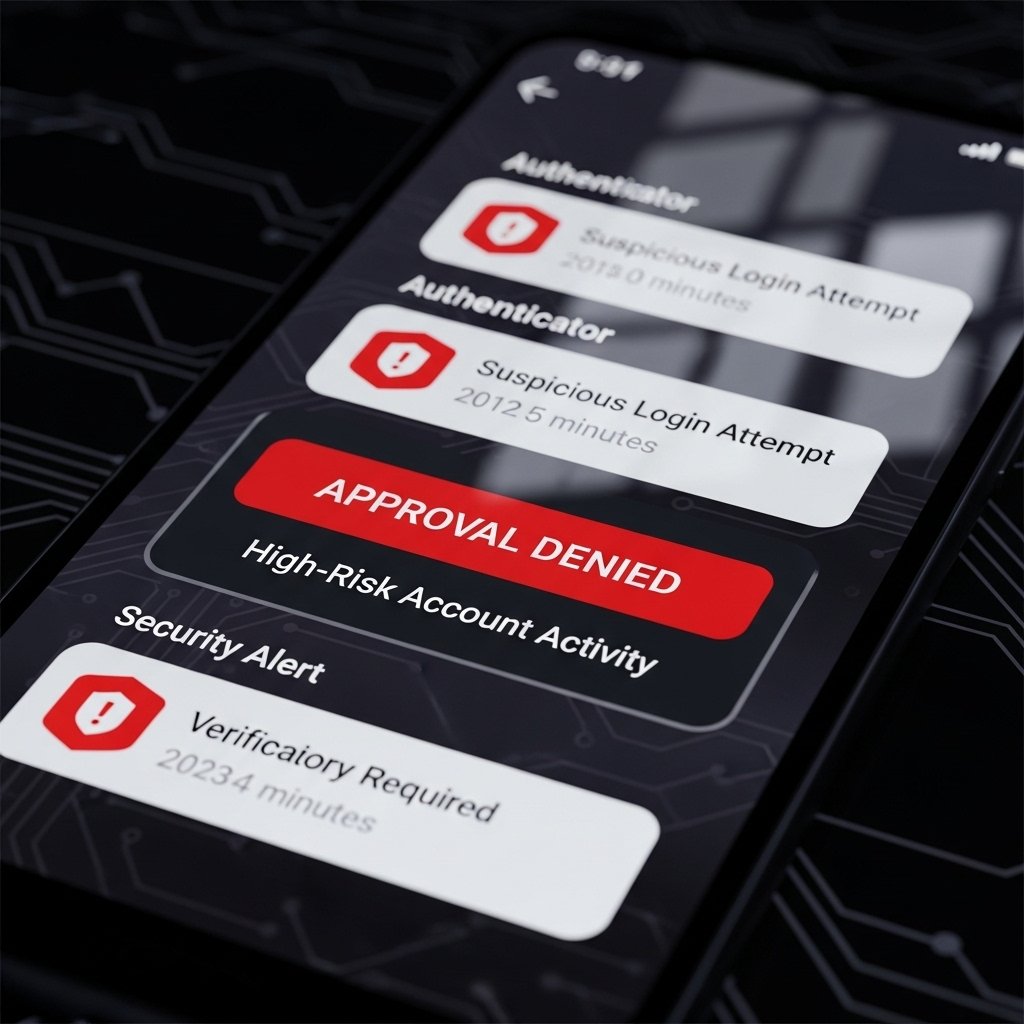
Authentication apps pushed approval requests while devices stayed unused. Denied prompts continued across several days. Pattern frequency indicated brute force attempts blocked only by secondary verification layers.
Customer Support Confirming Multiple Active Sessions
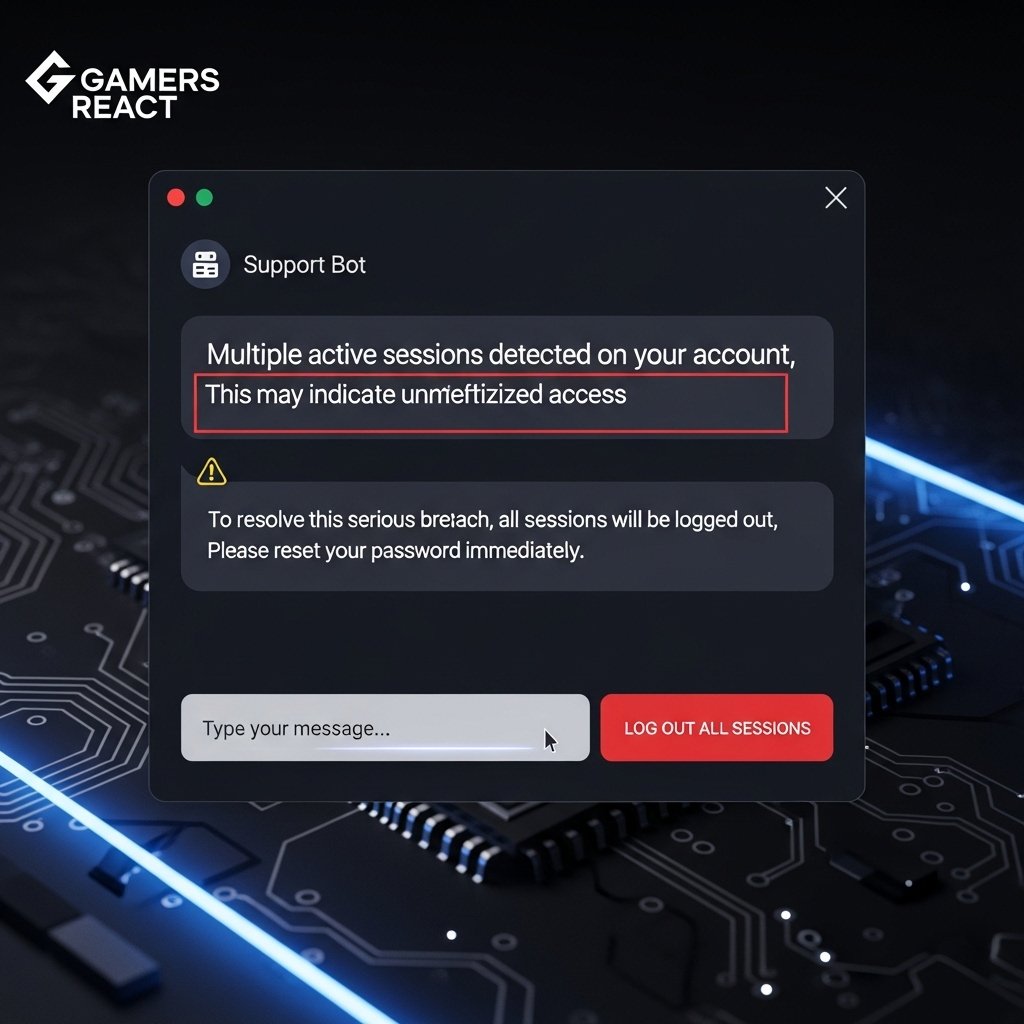
Support chat transcripts confirmed simultaneous sessions from different regions. Session termination removed unknown access temporarily. Reappearance followed within days. Support guidance emphasized stronger authentication due to repeated breaches across the same credentials.


